Use case
Data & IP Exfiltration
Identify unauthorized data transfers and safeguard valuable IP with real-time detection.
The Problem
Every enterprise faces an expanding range of data and intellectual property (IP) sources, potential exfiltration destinations, and methods of moving information out. This multifaceted environment creates a real risk of data slipping away unnoticed—whether accidentally or maliciously.
Key challenges
- Proliferation of data sources (corporate drives, endpoints, SaaS apps)
- Diverse exfiltration methods (browser, cloud, collaboration tools and CLI)
- Inability to correlate isolated events into actionable insights
The Anzenna Solution
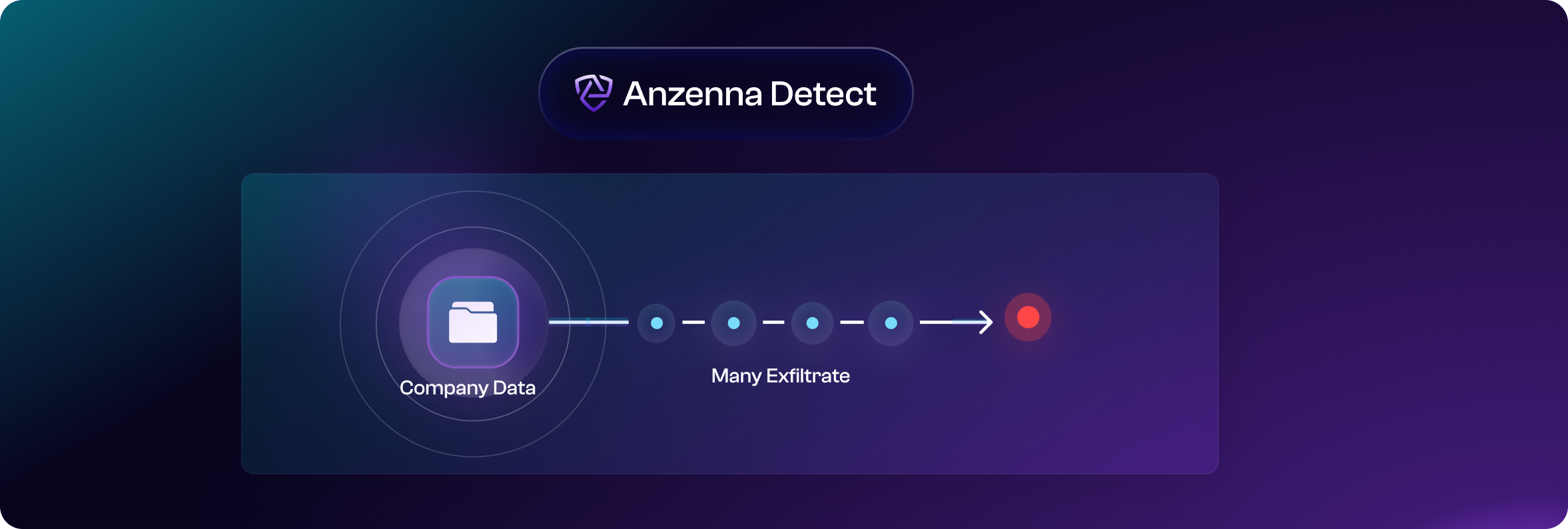
Anzenna’s graph-based, agentless approach brings order to chaos by correlating events in real time.
Complete Visibility
- Monitor exfiltration activities without installing endpoint agents
- Track critical channels (email, cloud storage, collaboration apps)
Holistic Data Movement View
- Unify events into an integrated data lineage graph
- Highlight suspicious patterns (e.g, SharePoint → personal Dropbox)
Risk-Based Remediation
- Block high-risk actions in real time
- Prioritize alerts based on severity
AI-Powered Pattern Detection
- Detect toxic combinations (e.g. download + external upload + external scp)
- Build clear trails of suspicious activity
AI-Powered Actionable Context
- Provide user identity, file metadata, and destination details
- Enable rapid investigation and remediation
Other Related Use Cases
SaaS Threats
Protect your data by preventing employees from transferring sensitive data to unauthorized third party applications.
Insider Cloud Data Exfiltration
Shield your cloud data from unauthorized and inadvertent leaks with proactive oversight.

Identity Threats
Safeguard against credential theft and account takeovers with continuous, real-time vigilance.

